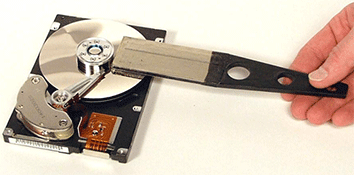
Degaussing uses an electromagnetic field to erase the data on a hard drive disk completely, as well as destroy the core components of a hard drive, and deleting the servo firmware, rendering it useless even if recovered.
Which cybersecurity risks does data destruction tackle?
A breach is the cybersecurity threat most people probably think of when they ponder what could happen due to insufficient data destruction. Most organizations collect and store sensitive or personally identifying information on its employees and customers, for example. Yet, once those employees or customers move on, businesses may hold onto their data for a little while but eventually want to remove it from their systems so they are not liable for fallout from a breach.

Cybercriminals look to compromise organizations for this very reason; and they do not limit their efforts to data being actively used by an organization. Data at rest, in storage, and in transit are all at risk. And threat actors know that users and organizations often rid themselves of physical devices without completely wiping them of data.
Should destroying data be high priority?
IT executives have a growing number of challenges to overcome regarding cybersecurity. Some of them may wonder if data destruction (or lack thereof) is a genuinely confirmed risk or merely a theoretical one. Substantial evidence shows that companies cannot afford to overlook data destruction as they iron out their cybersecurity plans.
Data destruction should not be overlooked
Cybersecurity is a hot topic for organizations, which are increasingly being targeted by cybercriminals for their troves of valuable PII. Data that is no longer useful to an organization is still a goldmine for threat actors. As the saying goes: One person’s trash is another person’s treasure.
And while organizations might spend a fortune on protecting their active data from getting into the wrong hands, what’s often overlooked is how inactive or old data is improperly secured or destroyed. Removing all traces of old data is important for saving consumers from continued exploitation, plus it sends a message to criminals that your organization has air-tight defense—even around its dumpsters.